Application Layer
# Application Layer
# Network Application Architectures
 Examples:
Examples:
- Webmail
 Examples:
Examples: - File sharing
- Bittorrent
# CS vs P2P File Distribution

# Client Server
- The server must transmit one copy of the file to each of the N peers. Thus the server must transmit NF bits. Since the server’s upload rate is us, the time to distribute the file must be at least NF/us.
- Let $d_{min}$ denote the download rate of the peer with the lowest download rate, that is, $d_{min} = min {d1, dp, . . . , dN}$. The peer with the lowest download rate cannot obtain all F bits of the file in less than $F/d_{min}$ seconds. Thus the minimum distribution time is at least $F/d_{min}$. $$D_{CS} \ge max{\frac{NF}{u_s},\frac{F}{d_{min}}}$$ From this we can observe that distribution time increases linearly with the number of peers N.
# P2P
- To get this file into the community of peers, the server must send each bit of the file at least once into its access link. Thus, the minimum distribution time is at least F/us.
- The peer with the lowest download rate cannot obtain all F bits of the file in less than $F/d_{min}$ seconds.
- The total upload capacity of the system as a whole is equal to the upload rate of the server plus the upload rates of each of the individual peers, that is, $u_{total} = u_s + u_1 + … + u_N$. The system must upload F bits to each of the N peers, thus delivering a total of NF bits. The minimum distribution time is also at least $NF/(u_s + u_1 + … + uN)$.

# Process Communication
Network applications on different hosts need a way to communicate with each other (sometimes across different operating systems). Client: process that initiates the communication Server: the other part of the pair
# Addressing Processes
To receive messages, a process must have an identifier. Each host has a unique IP address but this is not enough as there are many processes which can be running on the same host. A port number is needed to identify the receiving process/socket: HTTP server: 80 Mail server: 25
# Transport Service Requirements
- Data integrity: the amount of fault tolerance an application needs
- Throughput: rate which sending process can deliver bits to receiver. Because communication lines are shared, some bandwidth-sensitive applications (such as multimedia) may need a set throughout value.
- Timing: the amount of latency. An example guarantee might be that every bit that the sender pumps into the socket arrives at the receiver’s socket no more than 100 msec later. Such a service would be appealing to interactive real-time applications, such as multiplayer games.
- Security: encryption
# Application Layer Protocols
An application layer protocol defines:
- The types of messages exchanged, for example, request messages and response messages
- The syntax of the various message types, such as the fields in the message and how the fields are delineated
- The semantics of the fields, that is, the meaning of the information in the fields
- Rules for determining when and how a process sends messages and responds to messages
# HTTP
The Web’s application layer protocol is HTTP.
# Electronic Mail
A typical message starts its journey in the sender’s user agent, travels to the sender’s mail server, and travels to the recipient’s mail server, where it is deposited in the recipient’s mailbox. When Bob wants to access the messages in his mailbox, the mail server containing his mailbox authenticates Bob (with usernames and passwords)
 Each user agent uses a separate mail server rather than directly connecting with each other such that there is some recourse (able to keep retrying to send a message) when the destination is currently unreachable.
Each user agent uses a separate mail server rather than directly connecting with each other such that there is some recourse (able to keep retrying to send a message) when the destination is currently unreachable.

# SMTP
The heart of Internet electronic mail is SMTP, which allows for the transfer of messages.
# Mail Access Protocol
SMTP is a push protocol. Mail access protocols are needed to retrieve mail from the mail server via a pull operation:
# DNS
Many application protocols are built on top of DNS.
# BitTorrent
The most popular P2P protocol for file distribution is BitTorrent
# Distributed Hash Table
Another application of P2P is a Distributed Hash Table
# Socket Programming
How are network applications actually created? Processes running on different machines communicate with each other through sockets.

# TCP
Network applications may communicate through TCP, and hence the connection socket must support TCP. TCP provides a reliable byte-stream service:
 Basic byte I/O classes in Java
Basic byte I/O classes in Java

# Client
The client must perform the following operations:
- Open TCP connection to the server
- Send data
- Receive data on the connection
- Close the connection

# Server



# Encoding/Decoding
To transfer a string between two processes over the network, we must decide how to represent the string as a sequence of bytes.
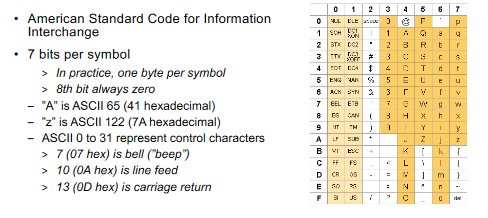
# ASCII
# UTF-8
- Unicode Transformation Format – 8-bit
- Variable length encoding
- Up to four bytes per symbol
- The first 128 are the same as for ASCII
- Backwards compatibility – ASCII text is also valid UTF-8
- Dominating format on the Web

# Helpful Java classes

